Quick Start
1. Launching the program for the first time
|
The program interface is straightforward and easy to use. As shown in the screenshot at the right, there is a menubar (1) and a toolbar (2)
to manage the program. There are also hot key combinations to provide a quick access to the main menu options. The largest section is an
information pane (3) showing the progress and status of the program. There is a context help pane (4) below which provides brief help
information. | 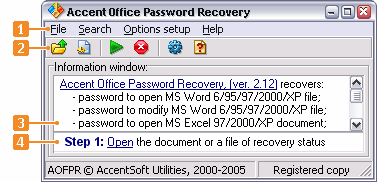 |
2. Password recovery
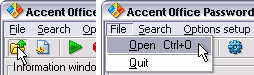
1. Open a designated file. Use the menu option File ···> Open or hot key combination (Ctrl+O).

2. The information pane will show the details about the file that program was able to recover.

3.
If the mechanism of file protection is recognized, you can start password recovery immediately. The information pane will inform you that the menu option Search ···> Start is available. You can optionally access it using hot key combination (Ctrl+S).
4. After you Search for a password, you may get more than one result depending on a type of file chosen and password type. Thus...
![]() Microsoft Money 99/2000/2001
Microsoft Money 99/2000/2001
• Database password will be recovered almost immediately because of the protection type used.
![]() Microsoft Access 6/95/97/2000/XP
Microsoft Access 6/95/97/2000/XP
• Database password will be recovered almost immediately because of the protection type used.
![]() Microsoft Word 6/95
Microsoft Word 6/95
• Password to edit a file will be recovered almost immediately because of the protection type used.
• Password to open a file will be recovered (or recovery will fail) almost immediately because of the protection type used. Success of the recovery procedure depends on the size of the text in the file.
![]() Microsoft Word 97/2000/XP,
Microsoft Word 97/2000/XP, ![]() Microsoft Excel 97/2000/XP
Microsoft Excel 97/2000/XP
• Password to edit a file will be recovered almost immediately because of the protection type used.
• Password to open a file can be found by using one of the three available algorithms. The program will give you a suggestion which one to use as well as ask you for some search criteria (Task setup):
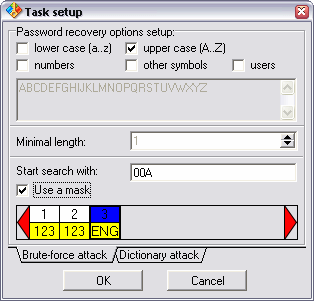
• Brute-Force Attack: The most reliable algorithm but time consuming. The program will generate and try all the passwords within a specified range. The range can be defined as follows: 1. The range of the characters to use for password generation. You can either use the predefined set or check the "users" box and create your own set. 2. A minimum length of the password. The unregistered version is limited to a maximum password length of 4 characters automatically. The registered version allows up to 15 characters. 3. You can also define a password to start the search with.
[ ! ] The more refined your search criteria are, the more quickly a password will be recovered. Therefore try to recall as many details of the forgotten password as possible. Even an approximate idea of the characters type and the length of the password (for example, only small letters and 4-6 characters) can significantly limit the choices available and thus the time needed for a search. |
 |
• A Brute-Force Attack With a Mask: An extended variant of the brute-force attack. This attack is useful if you know a part of the password and there is no need to search all the variants. Using the advanced program features, you can specify the password generation rules and define all possible values individually for each password character. This shortens the password search time.
[ ! ] For example, you can set the password to be generated with uppercase letters in the first position, with lowercase letters in the second, third and fourth positions, with the constant character "-" in the fifth position and a number (0-9) in the sixth position. In this example, the passwords will be generated in the range "Aaaa-0" to "Zzzz-9". You can also specify a limited range of characters individually for each position.
• Dictionary attack: The quickest algorithm but less reliable than the brute force methods. It assumes that you have a dictionary; that is, a text file made of several lines, one word per line. Define the dictionary location on your machine, and the program will automatically try all the combinations listed in the dictionary. This attack works best when a password is a significant word and can be included in some dictionary.
In addition to a normal search, the advanced program features allow you to transform words found in the dictionary. You can use program settings to change the case of letters, interchange adjacent characters, and skip characters. These features increase the probability of successfully recovering a password in a shorter amount of time.
You can compose a dictionary yourself or download some available at www.Outpost9.com. You can download a large dictionary here that contains more than 3 million of words (in the Roman alphabet).
Download now! (6.76 Mb)
[ ! ] Note that most languages contain no more than a few thousand significant words (even including related grammatical forms), so they can all be tried by the program within seconds. The number of non-significant character combinations is tremendously bigger (for example, there are 308,915,776 choices for a six-character password). So if there is any possibility that your password is a significant word, start your search with the dictionary attack.
After you confirm the algorithm choice, the program will start a search which can be monitored in the information pane.
3. Program setup and tuning
 • Minimize to a system tray. When you minimize the program, it's icon will be located not in the Taskbar but in the System tray next to clock. This is convenient for a program that may run for a long time and takes a significant part of a computer screen.
• Minimize to a system tray. When you minimize the program, it's icon will be located not in the Taskbar but in the System tray next to clock. This is convenient for a program that may run for a long time and takes a significant part of a computer screen.
• Show context help. Adds a help pane below the information pane.
• Save the state of searching each. Specify the interval for saving the state of search recovery to a Password Recovery Status (PRS) file. You can use this file to resume searching following an interruption (the program closed by mistake, a power failure, etc.).
• Mask character. Select a symbol to mark a missing character for the Brute-Force With Mask Attack.
• Application's priority. Determine how system resources (mostly the processor time) are used by the program during the operation:
• normal – the application will be allocated equal resources in relation to other applications operating in the system;
• idle (recommended) – the application will use all free resources of the system;
• high – the application will use most of the resources of the system. This is the most efficient mode for the program, but other programs may operate with a significant decrease in performance;
• low – the application will use the minimum amount of system resources. This will affect the program performance but will not affect the performance of the system.
4. Program registration
| Program registration consists of two stages:
• Paying for a registration key.
Go to the Registration page and submit all the information needed to pay for a registration of the product that you want to purchase. After the payment is received you will be notified by email. This email will contain your exclusive registration key.
• Unblocking the program. Run the program after receive the confirmation email. Choose "Registration" in the Help menu (or press hot key combination Ctrl+R). Copy your registration key into the appropriate field. (Do not type it in manually! Use highlighting and hot key combinations Ctrl+C and Ctrl+V to ensure it is entered correctly.) Then press "OK". The program will verify your key and, if valid, will congratulate you with a successful registration. |  |
If you get a message that the registration key is not valid but you are certain you entered it correctly, please contact support.
News&Releases
Passcovery 25.01 Password Recovery with GPU Acceleration: Support for NVIDIA Blackwell, Intel Arc Battlemage, New Mobile RDNA Ryzen Graphics, and Faster Recovery for Microsoft Office and TrueCrypt. In the January update, we added support for modern graphics architectures: NVIDIA Blackwell (SM10, SM10.1, SM12), Intel Arc B-Series (Battlemage), and mobile RDNA 3.5 Ryzen. We have also made additional optimizations for SHA-512, increasing the speed of password recovery for Microsoft Office 2013-365 and TrueCrypt. Improvements to the program core further enhanced overall performance, accelerating password recovery. 30.01.25
Knowledge base
How to Decrypt an Excel File Online When the Password is Lost
Recovering the password for a multivolume RAR archive
How to Decrypt an Excel File Online When the Password is Lost
Follow us
Partners